Crypto Wallets
1. The 2 components of a crypto wallet
It has the following:
a) Public Key
b) Private Key
The PUBLIC KEY is your crypto wallet’s receiving address.
You send this address to anyone to RECEIVE crypto from him/her.
Your PRIVATE KEY is used to SEND cryptos from your wallet to the recipient’s wallet.
Both the Public Key and Private Key are made up of a long string of numbers and alphabets. They are cryptographically RELATED.
This means that the wallet will know if a RANDOM Private Key is keyed in for a Public Key that represents your wallet, to send cryptos to some other wallet — and the transaction will not go through.
There can also be a PASSWORD to enable you to log into your crypto wallet.
This Password is different from your Private Key as the password’s main function is simply to enable you to log into your crypto wallet.
Any SENDING of cryptos requires you to know your Private Key which must be keyed in before you can send them.
Any RECEIVING of cryptos requires you to send your Public Key to your sender before he can send them to you (and the sender must have his own Private Key to his crypto wallet that he must key in before he can do this).
However, when you use a crypto exchange’s crypto wallet to store your cryptos, you will only have a Public Key, but not a Private Key.
The crypto exchange itself holds your funds for you and manages the Private Keys associated with those funds.
2. Forms
Crypto wallets that store your cryptos can be in the following forms:
a) Desktop wallet
– You download this type of wallet from the Internet into your desktop computer, as it’s a piece of software
– You log into it just like you would log into your email program, with a password
b) Mobile wallet
– Same as for desktop wallet
– You download and install the mobile wallet app from the App Store or Play Store into your mobile phone
– You log into it with a password
– Some mobile phones have biometric capabilities which enables you to log into your wallet using your fingerprint or face
c) Hardware wallet
– These wallets look like a bigger USB or Pen drive, with their only purpose to store your cryptos (not PDFs or other files)
– 2 of the top hardware wallets are found at the following sites:
d) Paper wallet
– This is just a piece of paper that has printed on it your wallet’s Public Key and Private Key.
– You need to store this paper carefully somewhere where nobody can find it.
– You should print a few copies of this and keep them in separate places in case you can’t remember or lose the original printout.
– It can come with a QR code of your Public Key that you can snap a photo of and send to someone you are receiving crypto from (just ensure you don’t include your Private Key in the same photo!).
e) Crypto Exchange wallet
– You will only have your Public Key.
– The exchange manages the Private Key associated with your Public Address.
– Crypto exchanges will have additional measures in place to prevent hacking into your crypto account, including getting you to create a strong password, binding your email and your mobile phone number to your account to receive verification codes via email and SMS, activating your 2FA (using Google Authenticator) and others.
BTW I have used ALL of the above methods to store my cryptos. Each has its own pros and cons so it’s hard to say which is better than the other. I have owned 2 models of the Trezor Wallet.
But the “safest” of them all is probably …the paper wallet!
It’s free (other than the paper and printing) and you can easily duplicate them for free as well. If you lose one of them you will have another in another location.
But if you lose your laptop, or mobile phone, or your hardware wallet, you can still recover them if you have written down your Public and Private Keys somewhere and then keying them in again after a re-installation and/or purchase of a new laptop/mobile phone/hardware wallet.
This recording of your Public and Private Keys and Passwords on paper which isn’t connected to the Internet is safer than typing them into your Notes app on your computer or mobile phone, or taking a photo of your Public and Private Keys and storing them in your Photo Albums — which can be accessed by anyone in possession of your phone.
So you’re back to paper anyway. So you might as well use a Paper Wallet!
This advice alone will have saved you a few hundred dollars it cost me to buy the Hardware wallet — but nobody could give me the proper advice way back then.
Having said that — a Paper Wallet cannot “send” any cryptos. You still need to download a wallet application/software (like “Electrum”) for this purpose, or use an online wallet (like “Metamask”) and then import your Public and Private Keys from your Paper Wallet into them. But once done you can delete the Wallet application/software, or remove your Public and Private Keys from your online wallet.
Also note that not all software wallets support all cryptos, so make sure you know which wallets you need before downloading or accessing them online.
Ok, now look at the attached image for the pros and cons of the various types of wallets.
Understanding how they work and their pros and cons is very important as your cryptos (and wealth) are stored there.
This will also set the stage for the various wealth creation/wealth multiplication systems to be revealed once the basics are understood.
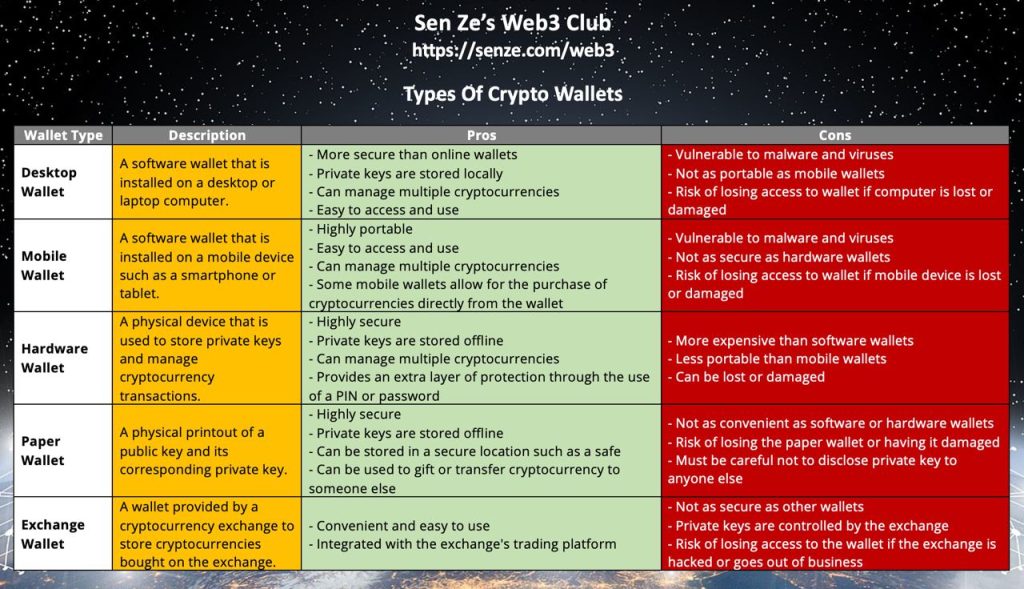
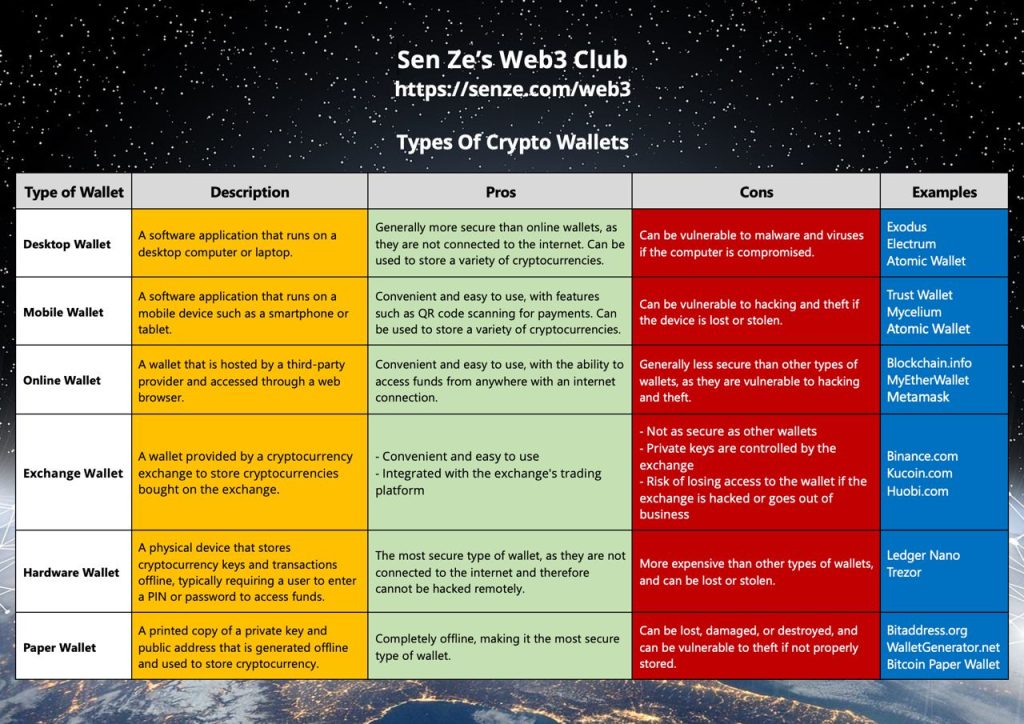
The sources for each type of wallet are shown in the blue column. I’ve also added “Online Wallets” (where you don’t have to download a full software or app).

This is how a crypto Paper Wallet looks like. Make multiple copies of it in case any is lost or becomes damaged. But the more copies you make, the more unsecure it is.